What is cloud edge security?
Cloud edge security protects the intersections of cloud computing and the physical world. As more devices integrate, organizations rely on cloud-edge security to safeguard data.
Workloads at the edge are often related to a company's main business, such as connected medical devices in healthcare, sensors on production lines, and retail point-of-sale systems. It becomes crucial to guarantee the smooth operation of these critical tasks and safeguard the processed data.
Cloud edge security involves implementing security measures on data sources to eliminate potential risks and enhance response times. It strategically positions firewalls, intrusion prevention and detection systems, and other advanced tools at the network's edge to find potential danger. Edge security offers a defense against malware, zero-day threats, and other vulnerabilities, especially as the attack surface expands.
Many organizations use cloud edge security solutions to securely access the internet and protect all network activity.
Benefits of cloud edge
Cloud edge's benefits range from offering low-latency experiences to connecting vehicle drivers to cost-effectively launching new services as a service provider. Working with cloud edge may also:
- Expedite service development. Without losing the robust functionality of a multi-tenant secure cloud, cloud edge architecture speeds up service development at the network borders using automated and easy delivery.
- Deploy services cost-effectively. Developers can establish new services with limited space and power at the network edge.
Components of cloud edge security
Protecting endpoints, data, and networks are all crucial components of cloud edge security.
- Endpoint protection. Edge computing devices may be found in various sizes and designs. IT departments handle vast volumes of remote devices, such as laptops, cell phones, and tablets. Cloud edge security keeps these devices safe on the edge networks.
- Data protection. Interconnected devices create massive volumes of data and require greater power to process. Edge computing brings processing and storage capabilities closer to data sources. It transfers data from the edge to the cloud while managing the load and offering security as required.
- Network protection. This element allows organizations to securely connect their internal resources over the internet. Cloud edge security guarantees users and systems have access without compromising on speed.
Cloud edge computing security best practices
Working on the edge necessitates following certain best practices, much like other types of cybersecurity.
- Implement zero-trust access across the board. A zero-trust security paradigm is a cybersecurity strategy that doesn't rely on predetermined trust levels. In other words, individuals and gadgets are not trusted by default. This applies to both devices inside and outside the network boundary.
- Control and manage edge devices internally or reject their connections. The internal IT department needs to set up and manage their edge devices using agents to secure them. These agents maintain and update the device's security; they know if there’s a compromise. If a device is not correctly regulated, it will either be considered a public device or its connections will be denied entirely.
- Use artificial intelligence and machine learning tools to monitor activity across edge devices. Intelligent edge devices have sensors and other data collection tools. These gadgets produce significant data. They can point toward malicious behavior when observed properly. Then, organizations can identify dangers in real time and take action to prevent them.
- Isolate edge devices within the public cloud infrastructure. Edge devices should be isolated to the public cloud infrastructure if a zero-trust network isn’t in place. These devices stay protected against any possible danger. Moreover, this stops devices from being a gateway for hackers looking for weaknesses within a company’s network.
Edge computing vs. cloud computing vs. fog computing
The main difference among edge computing, cloud computing, and fog computing is the data processing location.
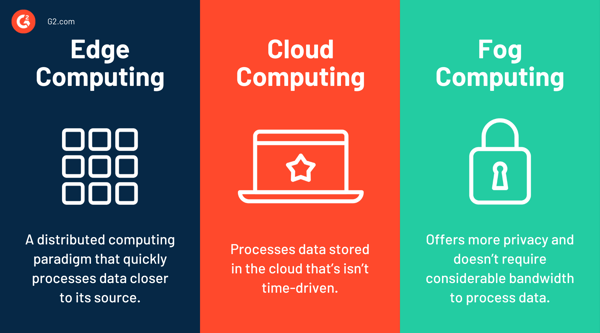
Edge computing is a distributed computing paradigm that processes data close to its source. It facilitates fast processing and produces actionable results in real time.
Cloud computing is used to process data that’s not time-driven. The data is stored in the cloud, which isn’t close to the source. When there is limited or no connectivity to the cloud, organizations go for edge computing.
Fog computing offers a decentralized computing system. It provides more privacy and needs less bandwidth to process data. However, it can be complex and more challenging to understand.
Learn more about cloud computing and understand how it delivers shared resources.
 by Sagar Joshi
by Sagar Joshi
 by Kelly Fiorini
by Kelly Fiorini