Security management safeguards an organization’s assets against threats. It secures physical facilities, IT necessities, employees, and other organizational requirements.
Identifying and documenting assets while implementing comprehensive policies and processes are security management’s primary objectives. Protecting organizational assets against threats ensures their integrity, confidentiality, and availability.
Security management covers cloud security as a part of its overall strategy. Many security management programs implement cloud access security broker (CASB) software to adopt a protection layer and enforce policies regarding employee access to the cloud.
Various specialized domains come from security management. They address the domain-specific aspects of safeguarding a company against threats.
Security management mitigates diverse threats faced by an organization. These digital risks are grouped into two categories.
Robust security management systems stop an organization’s assets from being compromised in any adverse situation. It offers multiple other benefits.
There are three fundamental phases: assessment, awareness, and activation.
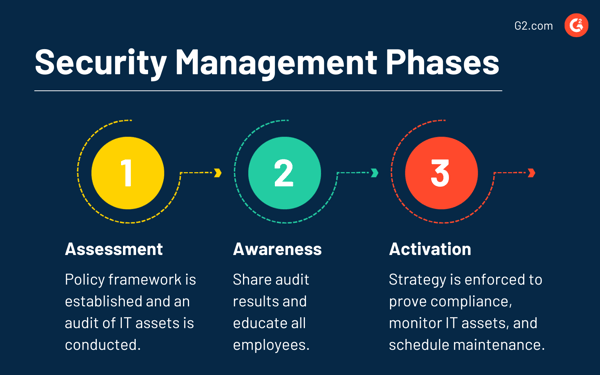
Here’s what they mean:
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) suggest a few best practices to implement security management. Professionals can find it in ISO/IEC 27001. Here’s a brief overview:
While information security management and cybersecurity share commonalities and often overlap, they have a distinct scope. Information security management comprises securing physical premises, facilities, and equipment, not just digital assets. It protects the confidentiality, integrity, and availability of an organization's intellectual property, trade secrets, and other proprietary information.
Cybersecurity focuses on securing electronic systems, networks, and connected devices against cyber threats like malware and malicious hacking. It emphasizes protecting digital data while preventing risks associated with cyber threats, which can disrupt operations and compromise an organization’s security posture.
Both are equally important for an organization’s security. They ensure data and assets are safe and vulnerabilities are identified and remediated before attackers can exploit them.
Learn more about how to manage vulnerabilities and reduce security risks to your organizations.
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.
What is internet protocol? Internet protocol connects devices and facilitates data...
 by Sagar Joshi
by Sagar Joshi
What are IoT devices? Internet of Things (IoT) devices are hardware instruments that collect...
 by Sagar Joshi
by Sagar Joshi
What is cybersecurity? Cybersecurity refers to actions taken to combat threats against...
 by Sagar Joshi
by Sagar Joshi
What is internet protocol? Internet protocol connects devices and facilitates data...
 by Sagar Joshi
by Sagar Joshi
What are IoT devices? Internet of Things (IoT) devices are hardware instruments that collect...
 by Sagar Joshi
by Sagar Joshi


